OpenClaw Enters OpenAI’s Orbit
What the move signals about our multi-agent future.
OpenClaw is an open-source, local-first personal agent platform that lives in your existing chat apps and can take real-world actions on your behalf. The mission is to make a trustworthy, user-owned agent practical, so the default way to ‘use a computer’ becomes delegating intent, not clicking interfaces.
Capability Outran Trust
Knowledge work is already capacity-constrained: too many inputs, too many contexts, too little time. The work is often the glue: triage, scheduling, follow-ups, copying, pasting, reminding, reconciling. Humans are good at judgment; we are tragically overqualified for clerical loops.
Most people patch the problem with a pile of narrow tools: calendar apps, inbox rules, RPA scripts, macros, notetaking systems, and now chat assistants. These help, but they largely keep the user in the loop as the human API between intent and execution.
Shortcomings of current solutions: 1) Context is fragmented across apps. 2) Assistants are often SaaS-first, which makes trust and privacy hard. 3) ‘Tool use’ is fragile: permissions, OAuth, and edge cases become product tax. 4) Interfaces don’t match attention: people live in messaging surfaces, but automation often requires hopping into dashboards.
A Local‑First Agent That Acts
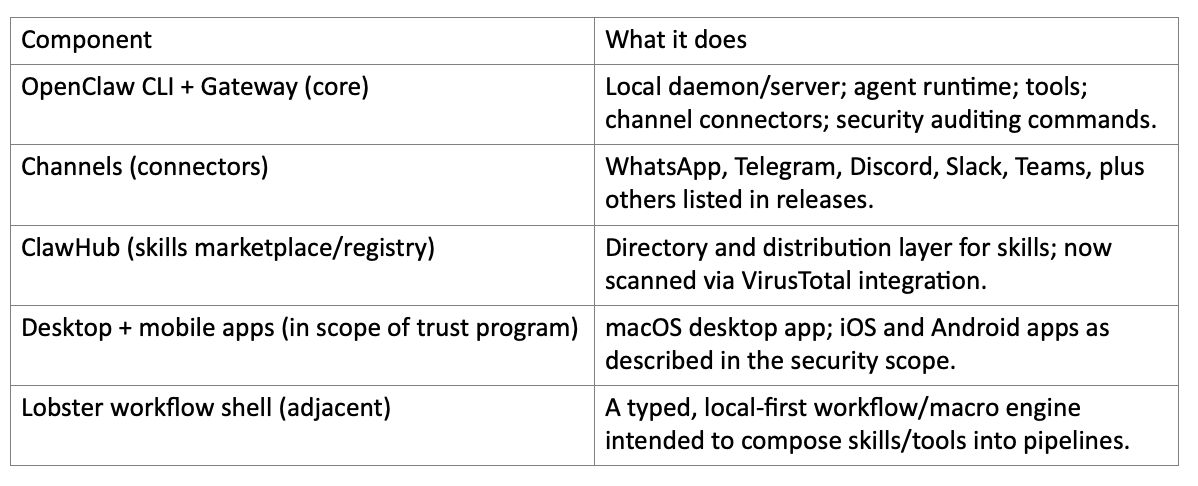
Instead of a new productivity app, OpenClaw acts like a background runtime: you message it; it acts; it reports back. Move the agent to where you already talk, and move trust to where you already have control. A gateway daemon runs on a machine you control (laptop, homelab, or VPS), connects to chat channels, and brokers tool execution and model calls.
The value proposition is the completed loop. For example: You forward a flight email → the agent extracts the confirmation code → opens check-in → selects a seat → sends you the boarding pass link. OpenClaw is a catalogue of these closed-loop wins.
Durability will come from compounding: a growing skill ecosystem, hardened security defaults, and an opinionated operational model that makes agents less scary to run.
The founder’s stated direction: security first, then reliability and polish, then broader model/provider support.
Use cases:
Inbox and message triage (spam removal, follow-ups, summaries).
Calendar operations (time-blocking tasks; conflict detection; weekly reviews).
Ops automation (SSH into a VPS, check a deploy, patch configs, redeploy).
Personal second brain workflows (summarize links, file notes, generate docs).
Smart home orchestration (Home Assistant / devices via skills).
Models Got Cheap, Interfaces Stayed Stuck
Pre-LLM assistants couldn’t reliably translate language into multi-step action. Early LLMs could talk but not act. Once models became competent planners and code-writers, the missing piece was a practical runtime that ordinary power users could host.
Voice assistants (Siri/Alexa) popularized ‘ask’ but not ‘delegate.’ ChatGPT popularized language interfaces; the 2024–2026 wave is shifting from ‘answers’ to ‘outcomes,’ multi-agent orchestration, long-running tasks, and new surfaces.
Agents became feasible when three curves crossed: model capability (tool use + long context), integration plumbing (APIs and skills), and distribution (chat as the universal UI). OpenClaw arrives exactly at that intersection.
Recent trends that make OpenClaw possible:
Multi-agent patterns are formalizing, with orchestrator + specialist-agent topologies.
Enterprises are beginning to accept ‘agents’ as a first-class interface, which drags standards and tooling behind it.
Security discourse is catching up fast, prompt injection and tool abuse are now treated as design constraints.
A Wedge in Personal Workflows, a Prize in Control Planes
OpenClaw’s core customer today is the ‘agent-capable’ user: developers, operators, and power users who are comfortable hosting software and treating security as real work. In the medium term, the stated goal expands to non-technical users, “an agent that even my mum can use” but that implies major product and safety evolution.
OpenClaw behaves like a consumer-grade agent operating system: a persistent runtime, a distribution surface (chat), and a marketplace (skills). That’s a category that doesn’t quite exist in a tidy Gartner box yet, so the company has to educate the market while building it.
Who OpenClaw caters to right now):
High agency: people who want software to do things, not merely answer.
High tolerance for configuration.
High concern for privacy/sovereignty (local/VPS).
High sensitivity to security trade-offs.
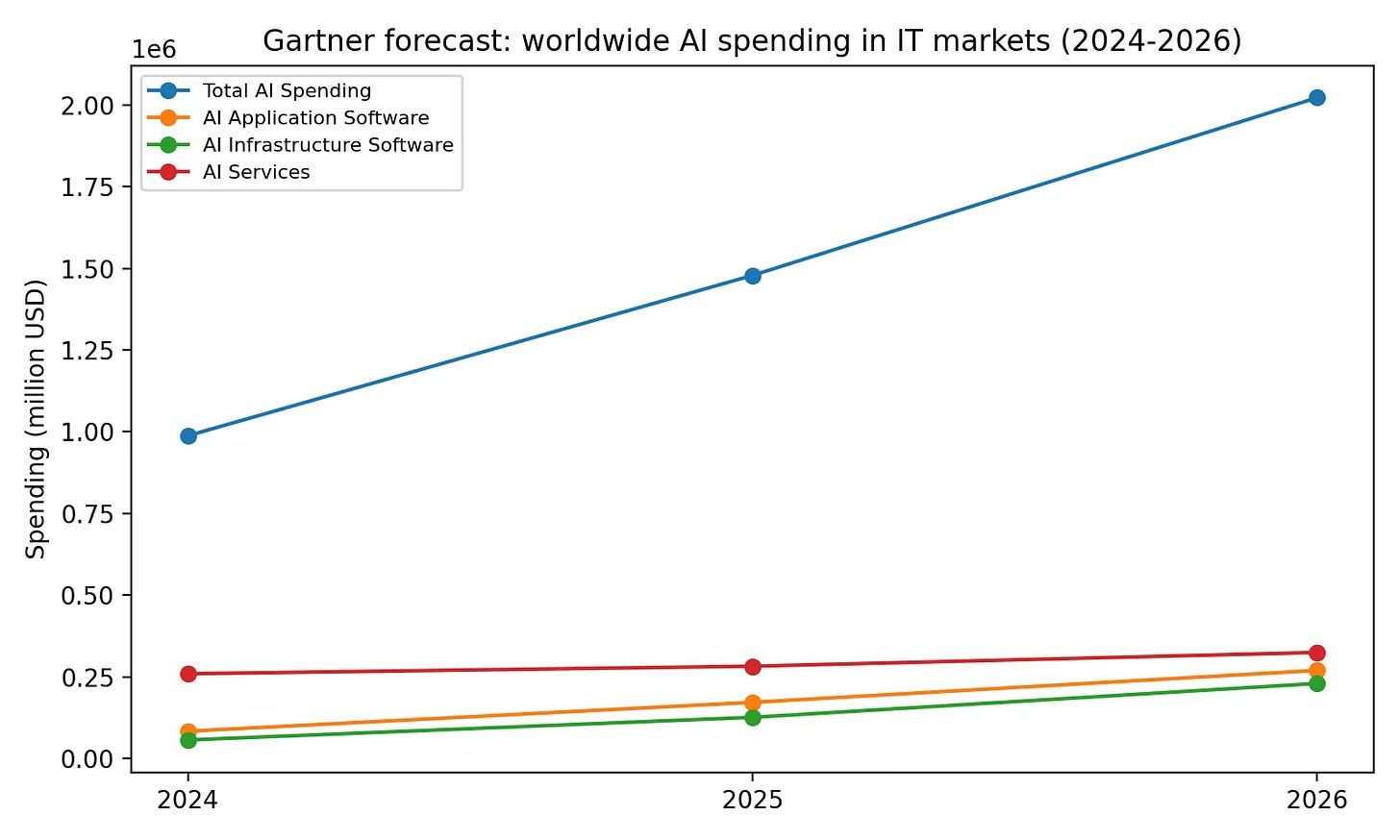
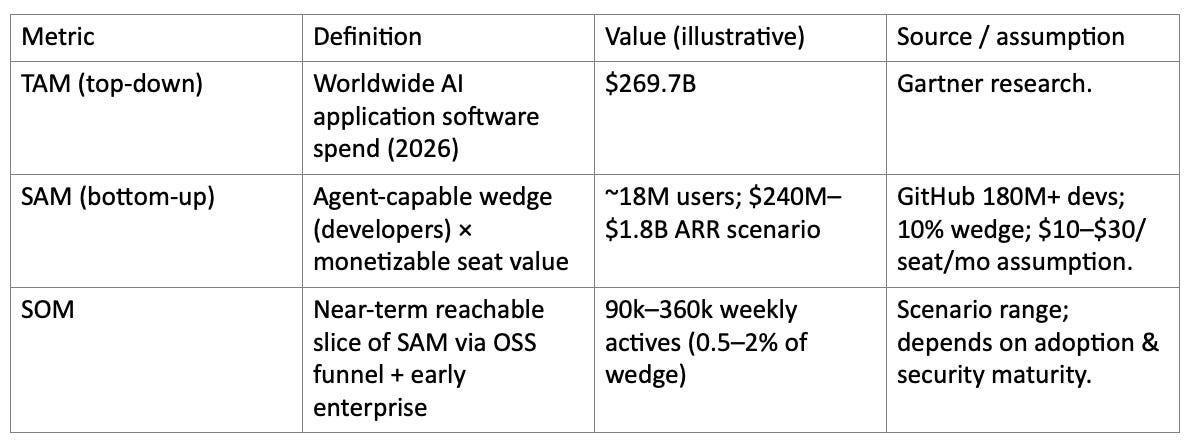
As a top-down anchor, Gartner forecasts worldwide AI application software spending of $269.703B in 2026. If you treat OpenClaw as a slice of that application layer: agentic productivity, automation, and orchestration, this is the broadest plausible ceiling.
A bottom-up SAM requires choosing a first ‘wedge’ population. A defensible wedge is developers and adjacent power users, because OpenClaw’s current operational model assumes comfort with hosting and security. GitHub reports 180 million-plus developers on the platform. If even 10% of that group becomes ‘agent-capable’ in the next few years, that’s an ~18M-user wedge.
To translate users into spend, you have to be explicit about what OpenClaw can monetize. Today, OpenClaw itself is open source and sponsor-funded; a plausible monetization layer would be enterprise management/security, hosted ClawHub services, and support contracts. As a placeholder model, an enterprise control plane at $10–$30 per seat per month applied to, say, 2–5M ‘agent seats’ globally yields a SAM on the order of $240M–$1.8B ARR.
Given OpenClaw’s current stage (rapid adoption, early security hardening, foundation transition), a realistic near-term SOM is dominated by the open-source adoption funnel rather than paid conversion. A conservative SOM framing is: capture 0.5–2% of the 18M ‘agent-capable developer’ wedge as active, weekly users (90k–360k), while building an enterprise offering that converts a small fraction of that base into paying accounts.
The Arena: OS Giants, AI Labs, Startups, and DIY Scripts
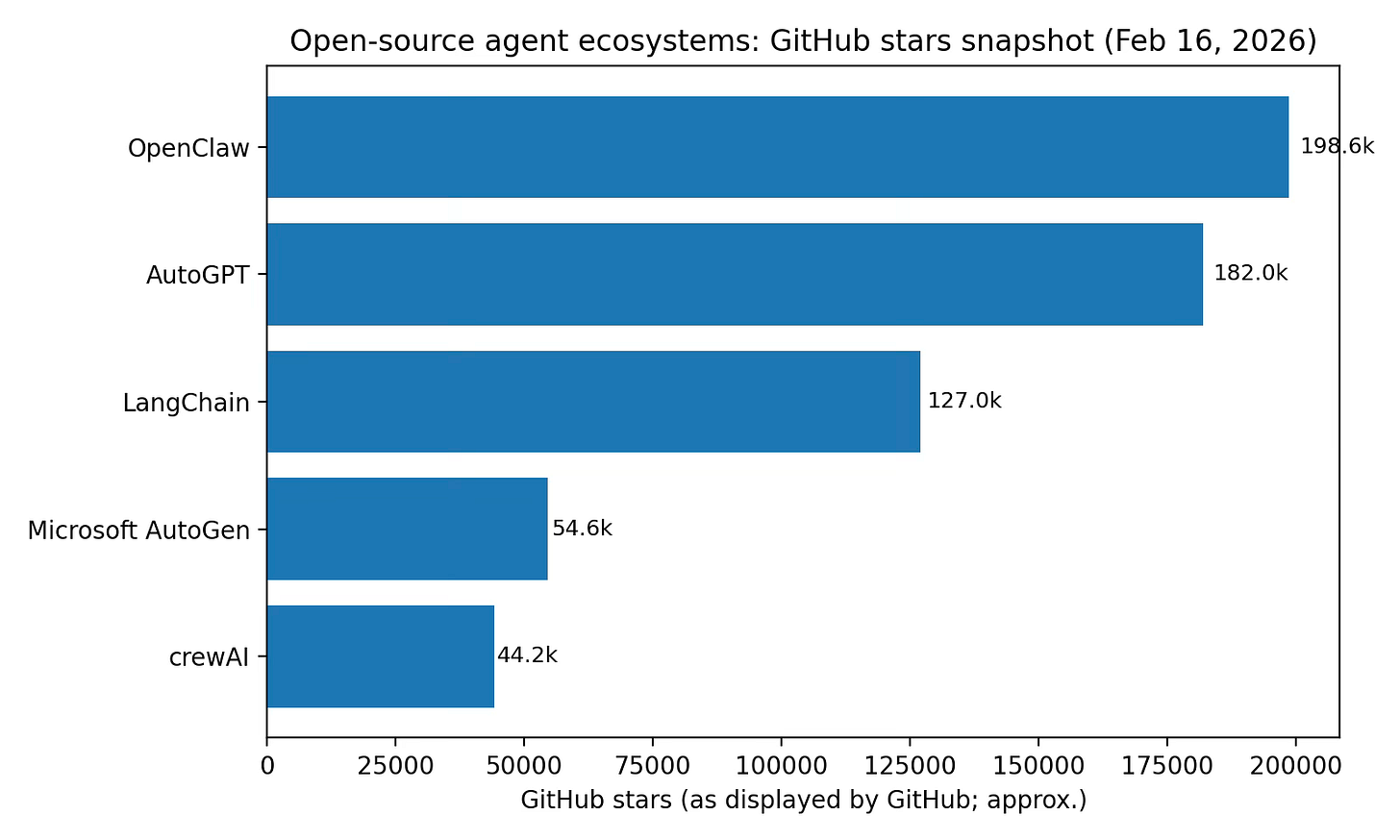
Direct competitors (open-source agent frameworks): AutoGPT, LangChain, Microsoft AutoGen, crewAI, and a long tail of orchestration libraries overlap in ‘agent runtime + tool use.’ OpenClaw’s differentiation is less about orchestration theory and more about productization: chat surfaces + local execution + skill registry.
Direct competitors (proprietary ‘agent products’): There is a parallel universe of closed platforms (labs and hyperscalers) shipping agents inside their own ecosystems. These often win on polish and model access; they often lose on sovereignty and extensibility. For OpenClaw, the practical competitive game is: interoperate where possible, differentiate where trust and customization matter.
Indirect competitors / alternatives: RPA (Robotic Process Automation), scripting (cron + Python), inbox rules, Zapier-like automation, and plain human assistants all compete as ‘ways to get outcomes.’ OpenClaw competes by collapsing integration + decision + execution into one conversational loop.
Inside the Machine: Gateway, Skills, Channels, Guardrails
Functionality / features (selected):
Chat-native control (agent as a contact).
Tool execution (shell, web fetch, APIs).
Skills system + marketplace.
Security defaults (pairing, allowlists, exec deny-by-default) and an explicit security audit command.
Architecture (high level): Gateway brokers authenticated sessions; runtime routes between model calls and tool calls; skills extend tool surface; outputs flow back to channel connectors. OpenClaw emphasizes running where you choose (laptop/homelab/VPS).
Development roadmap:
Security remains top priority.
Gateway reliability and polish.
Expand model/provider support.
In parallel, the trust program lays out a phased security function (threat model → public roadmap → comprehensive code review → triage function) with stated response SLAs.
Open Source, Optionality, Sustainability
OpenClaw is a community infrastructure rather than a conventional venture-backed SaaS. Funds flow back to contributors and dependencies. OpenAI already sponsors the project and OpenClaw will move to a foundation structure.
If OpenClaw ever chooses to become a ‘business,’ the obvious revenue layers are not the core runtime (which is open source) but the services around it: managed deployments, enterprise security/compliance tooling, private skill registries, and support. This is the classic open-core gravity well.
Maintainers, Security, Governance
Peter Steinberger (creator). OpenClaw began as a weekend project (initially “WhatsApp Relay”), then grew explosively. In Feb 2026, Steinberger announced he is joining OpenAI, while moving OpenClaw into a foundation to keep it open and independent.
Jamieson O’Reilly (Security & Trust). Brought on as lead security advisor as the project’s skill ecosystem expanded and the threat surface became impossible to ignore. His remit: threat modeling, code review scope/oversight, and establishing a triage function with response SLAs.
Bernardo Quintero (VirusTotal partnership). The Feb 2026 VirusTotal partnership post is co-authored and positions security scanning as a default layer for skills published to ClawHub.
The community (“Claw Crew”). OpenClaw’s speed comes from a familiar open-source flywheel: attention → issues/PRs → maintainers → ecosystem. The founder notes the need to add maintainers and establish processes to handle the influx.
OpenClaw’s immediate organizational challenge is incentives and process. Open-source velocity tends to create a backlog of promises; security work tends to create a backlog of debt. The right incentives make the boring work happen: reviews, threat modeling, release discipline, and saying no to flashy features.
Agent‑Native Computing That Deserves Trust
A plausible ‘five-year OpenClaw’ is stable layer in personal computing: a user-owned agent runtime that can be hosted anywhere, is secure-by-default, and is boringly reliable. It would have: (1) a hardened permission model, (2) a verified skill ecosystem with provenance and scanning, (3) strong interoperability with multiple model providers, and (4) a governance structure (foundation) that keeps the core open.
The founder’s stated direction already sketches the arc: broaden reach, do it safely, and keep OpenClaw open under a foundation while expanding support for “even more models and companies.”
The best outcome is a moat built from habit + ecosystem + trust. The only durable moat available to an open-source runtime is: a community that prefers your defaults, your governance, your threat model, and your distribution channels.